Data Security Management: Essential Strategies for Protection
Understanding Data Security Management
Data security management is a critical aspect of modern organizations as data breaches and cyber threats become increasingly prevalent. Organizations today are entrusted with vast amounts of sensitive information, including personal data, financial records, and intellectual property. As a result, robust data security management strategies are essential for protecting this information from unauthorized access, theft, or loss. This article explores the essential strategies for effective data security management and how organizations can implement these strategies to safeguard their data.
The Importance of Data Security Management
In an age where data drives decision-making processes and customer relationships, the importance of data security cannot be overstated. A breach in data security can lead to significant financial losses, reputational damage, and legal repercussions. For businesses, data breaches can also compromise customer trust and loyalty. Therefore, implementing effective data security management strategies is vital not only for compliance with regulations but also for maintaining a competitive edge in the market.
Key Components of Data Security Management
Data security management encompasses various components that work together to protect sensitive information. These components include data classification, access control, encryption, monitoring, incident response, and employee training. Understanding these components is essential for developing a comprehensive data security strategy.
1. Data Classification
Data classification involves categorizing data based on its sensitivity and the impact that its loss or unauthorized access would have on the organization. This process allows organizations to implement appropriate security measures tailored to the level of risk associated with each category of data. For instance, personally identifiable information (PII) should be treated with higher security measures compared to less sensitive data. By classifying data, organizations can prioritize their security efforts and allocate resources more effectively.
2. Access Control
Access control is a fundamental aspect of data security management that involves defining who has access to specific data and under what conditions. Organizations should implement the principle of least privilege, granting employees access only to the data necessary for their job functions. Role-based access control (RBAC) can help manage permissions and ensure that sensitive data is only accessible to authorized personnel. Additionally, organizations should regularly review and update access controls to adapt to changes in personnel or job roles.
3. Data Encryption
Encryption is a powerful tool for protecting data from unauthorized access. By converting data into an unreadable format, encryption ensures that even if data is intercepted, it cannot be easily accessed without the decryption key. Organizations should implement encryption for data at rest (stored data) and data in transit (data being transmitted over networks). Strong encryption algorithms and key management practices are essential for maintaining the confidentiality and integrity of sensitive information.
4. Monitoring and Auditing
Continuous monitoring and auditing of data access and usage are crucial for identifying potential security threats and ensuring compliance with security policies. Organizations should implement security information and event management (SIEM) systems that collect and analyze data from various sources to detect anomalies or suspicious activities. Regular audits can help assess the effectiveness of security measures, identify vulnerabilities, and ensure that data security policies are being followed.
5. Incident Response Planning
No security strategy is foolproof, and organizations must be prepared to respond to data breaches or security incidents when they occur. An incident response plan outlines the steps to be taken in the event of a security breach, including identifying the breach, containing the damage, and notifying affected parties. Organizations should regularly test and update their incident response plans to ensure their effectiveness and to train employees on their roles in the event of a security incident.
6. Employee Training and Awareness
Employees are often the first line of defense against data breaches. Therefore, providing regular training on data security best practices is essential for fostering a culture of security within the organization. Employees should be educated about the importance of data security, common threats such as phishing attacks, and how to recognize suspicious activities. Regular training sessions and awareness campaigns can empower employees to take an active role in protecting sensitive information.
7. Compliance with Regulations
Organizations must comply with various data protection regulations, such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS). Compliance not only helps organizations avoid legal penalties but also reinforces their commitment to protecting customer data. Organizations should stay informed about relevant regulations and ensure their data security management strategies align with compliance requirements.
8. Data Backup and Recovery
Data loss can occur due to various reasons, including cyberattacks, hardware failures, or natural disasters. Therefore, organizations must implement robust data backup and recovery strategies to ensure business continuity. Regularly backing up data to secure locations, both on-site and off-site, can help organizations recover quickly from data loss incidents. Organizations should also test their backup and recovery processes to ensure they are effective and efficient.
9. Third-Party Risk Management
Many organizations work with third-party vendors, which can introduce additional security risks. It is crucial to assess the security practices of these vendors to ensure they meet the organization's data security standards. Organizations should establish clear contracts that outline data protection responsibilities and conduct regular audits of third-party vendors. This proactive approach can help mitigate risks associated with outsourcing data management or processing.
10. Leveraging Technology for Data Security
Technology plays a vital role in enhancing data security management. Organizations should leverage advanced technologies such as artificial intelligence (AI), machine learning, and automation to improve their security posture. AI-driven security solutions can analyze vast amounts of data to detect patterns and anomalies, enabling organizations to respond to threats more proactively. Additionally, automation can streamline security processes and reduce the likelihood of human errors.
Conclusion
Data security management is an ongoing process that requires a multifaceted approach. By implementing essential strategies such as data classification, access control, encryption, monitoring, incident response planning, and employee training, organizations can create a robust security framework that protects sensitive information from unauthorized access and breaches. As the threat landscape continues to evolve, organizations must remain vigilant and adapt their data security management strategies to effectively mitigate risks and safeguard their data assets.
Future Trends in Data Security Management
As technology advances, the landscape of data security management is also evolving. Organizations must stay informed about emerging trends and technologies to enhance their data security strategies. Some future trends include:
1. Zero Trust Security Model
The zero trust security model operates on the principle of "never trust, always verify." This approach assumes that threats can originate from both outside and inside the organization, prompting a more stringent verification process for users and devices attempting to access data. Implementing a zero trust model requires organizations to continuously authenticate and authorize users, ensuring that only legitimate access is granted.
2. Cloud Security Solutions
As organizations increasingly migrate their data and applications to the cloud, cloud security solutions are becoming a priority. Organizations must adopt security measures tailored for cloud environments, including data encryption, access controls, and continuous monitoring. Additionally, understanding the shared responsibility model of cloud security is crucial for effectively managing risks associated with cloud adoption.
3. Artificial Intelligence and Machine Learning
AI and machine learning technologies are revolutionizing data security management by enabling organizations to analyze large volumes of data quickly and accurately. These technologies can help detect anomalies, predict potential threats, and automate responses to security incidents. By leveraging AI-driven security solutions, organizations can enhance their threat detection and response capabilities.
4. Privacy-Enhancing Technologies
With increasing concerns about data privacy, organizations are adopting privacy-enhancing technologies (PETs) to protect sensitive information. These technologies include data anonymization and pseudonymization, which can help organizations comply with data protection regulations while still deriving value from their data. Implementing PETs can enhance data security and privacy simultaneously.
5. Enhanced User Education and Training
As cyber threats become more sophisticated, the need for enhanced user education and training will continue to grow. Organizations should invest in ongoing training programs that not only cover basic security practices but also address emerging threats and social engineering tactics. Empowering employees with knowledge will strengthen the overall security posture of the organization.
6. Regulatory Compliance Evolution
As data protection regulations evolve, organizations will need to adapt their data security management strategies to remain compliant. New regulations may introduce stricter requirements for data handling, breach notification, and user consent. Staying informed about regulatory changes and proactively adjusting security measures will be essential for organizations to avoid penalties and maintain customer trust.
Final Thoughts
Data security management is an essential aspect of organizational success in an increasingly digital world. By implementing the strategies discussed in this article, organizations can create a strong data security framework that safeguards sensitive information from threats. As the landscape continues to change, organizations must remain agile, continuously adapting their strategies to address new challenges and emerging technologies. Ultimately, a proactive approach to data security management will not only protect valuable assets but also foster trust and confidence among customers and stakeholders.
Explore

Guarding Your Digital Fortress: Essential Data Protection Services for a Safer Tomorrow

Data Protection: Safeguarding Information in a Digital World

Ultimate Guide to Secure Data Protection Services: Safeguard Your Sensitive Information
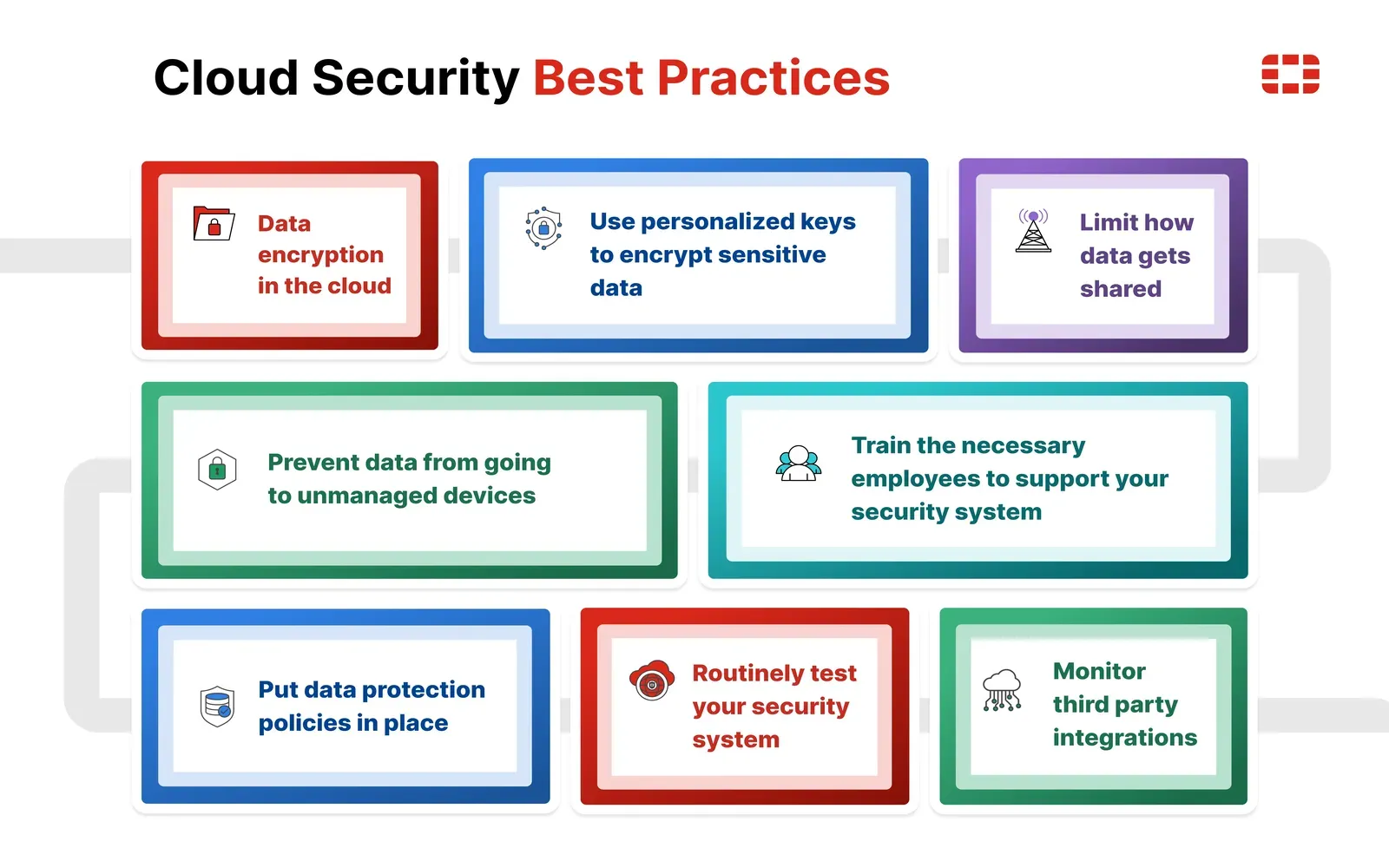
Strengthen Your Cloud Security: Best Practices & Strategies

Empowering Entrepreneurs: Essential Strategies and Resources for Small Business Success

Affordable Cloud Security: Protect Your Data Without Breaking the Bank

Best Cloud Security Services to Protect Your Business Data
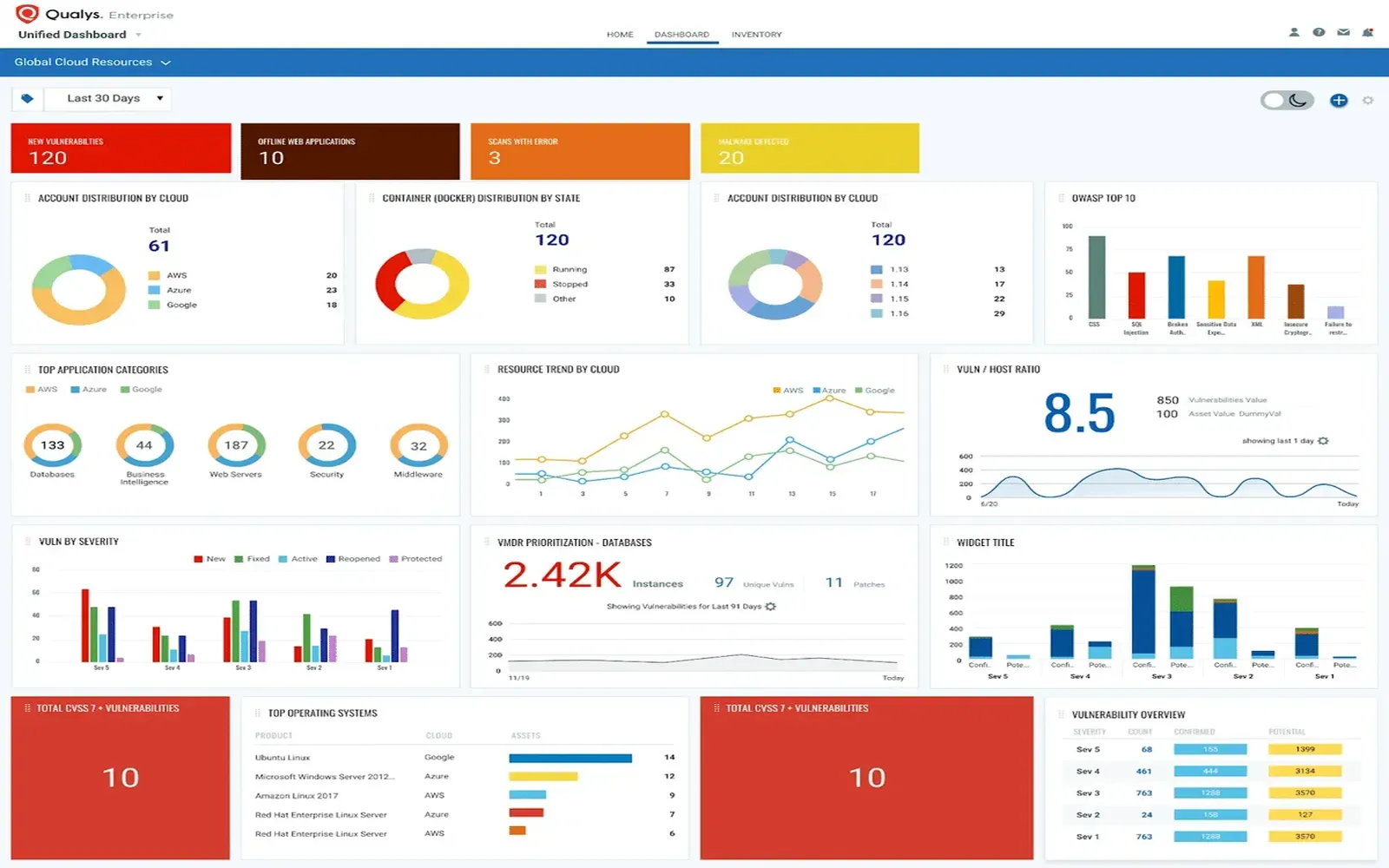
Top Cloud Security Providers: Safeguarding Your Data in the Digital Age
