Unlocking Network Insights: The Essential Guide to Top Network Monitoring Software
In today's digital landscape, securing cloud applications and safeguarding sensitive data has become paramount for small businesses navigating the complexities of cyber threats. With the rise of cyber security software tailored for smaller enterprises, organizations can leverage advanced solutions to protect their networks and ensure compliance. Notably, the Gartner Magic Quadrant for Cloud Security Posture Management highlights industry leaders, while effective data loss prevention measures and data leak prevention software are essential for mitigating risks. As we approach 2024, the best network security software, vulnerability scanners, and antivirus solutions will play a crucial role in fortifying business networks against evolving cyber threats.
Securing Cloud Applications
In today's digital landscape, securing cloud applications has become paramount for businesses of all sizes. As organizations increasingly migrate their operations to the cloud, the risk of cyber threats escalates. To safeguard sensitive data and maintain compliance with regulations, a multi-faceted approach to cloud security is essential. This includes implementing strong access controls, encryption, and regular security assessments.
One of the crucial steps in securing cloud applications is ensuring that only authorized users have access to sensitive data. This can be achieved through robust identity and access management (IAM) solutions that enforce strict authentication protocols. Encrypting data both in transit and at rest further protects against unauthorized access, as even if data is intercepted, it remains unreadable. Regular security assessments, including vulnerability scanning and penetration testing, help identify potential weaknesses in the cloud environment, allowing organizations to remediate them before they can be exploited.
Cyber Security Software for Small Business
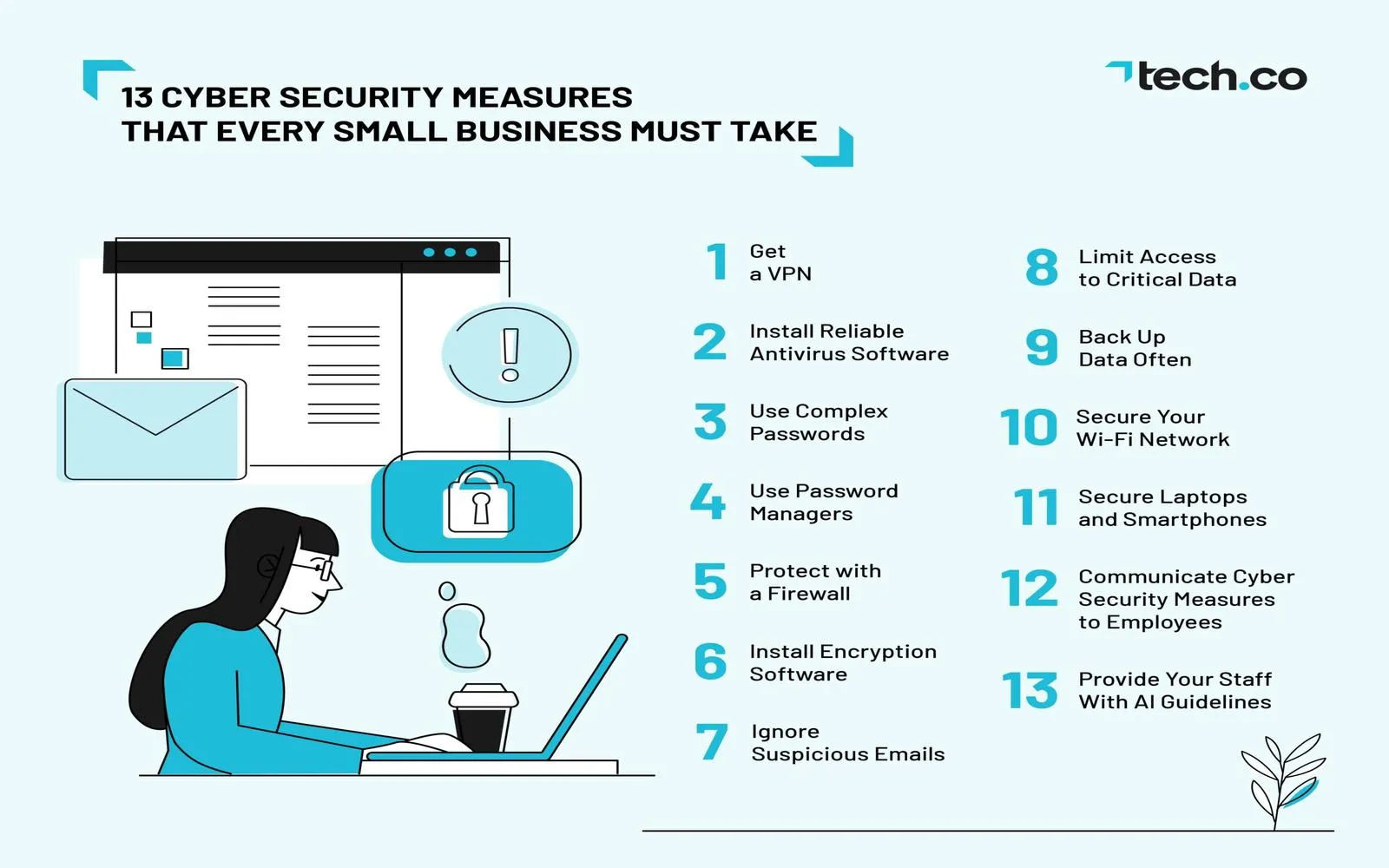
Small businesses often face unique challenges when it comes to cybersecurity. With limited resources and expertise, they may be more vulnerable to cyber attacks. Investing in the right cyber security software is crucial for protecting sensitive information and ensuring business continuity. Solutions tailored for small businesses should be user-friendly, cost-effective, and provide comprehensive protection against a variety of threats.
Key features to look for in cyber security software include antivirus protection, firewalls, and intrusion detection systems. Additionally, small businesses should consider solutions that offer automated threat detection and response capabilities. Cloud-based security services can also provide scalability and flexibility, allowing businesses to adapt their security posture as they grow. Regular employee training and awareness programs are equally important, as human error is often a significant factor in security breaches.
Best Network Monitoring Software in the USA
Effective network monitoring is vital for maintaining the health and security of IT infrastructure. The best network monitoring software in the USA provides real-time visibility into network performance, allowing organizations to identify and resolve issues before they escalate. Key features of top network monitoring tools include bandwidth monitoring, traffic analysis, and alerting capabilities.
Leading solutions often include customizable dashboards that provide insights into network activity, enabling IT teams to quickly detect anomalies or potential security threats. Additionally, integration with other IT management tools can enhance overall operational efficiency. Organizations should evaluate their specific needs and consider solutions that offer scalability, as the demands on network monitoring can grow with the business.
Cloud Security Posture Management Gartner Magic Quadrant
Cloud Security Posture Management (CSPM) has gained significant traction in the cybersecurity landscape, particularly as organizations continue to adopt cloud solutions at an unprecedented rate. The Gartner Magic Quadrant for CSPM provides a valuable framework for organizations to evaluate the leading vendors in this space. It categorizes companies based on their ability to execute and the completeness of their vision.
When selecting a CSPM solution, organizations should consider factors such as automation capabilities, integration with existing security tools, and support for multi-cloud environments. A robust CSPM solution can help organizations automate compliance checks, identify misconfigurations, and provide continuous monitoring of cloud resources. This proactive approach not only enhances security posture but also reduces the risk of costly data breaches.
Data Loss Prevention Measures
Data loss prevention (DLP) measures are critical for securing sensitive information against accidental or intentional loss. Organizations must implement a combination of technology, processes, and employee training to effectively mitigate the risk of data loss. DLP solutions typically focus on monitoring and controlling data transfers, both within the organization and externally.
Key DLP measures include the use of encryption, access controls, and data classification. By classifying data based on its sensitivity, organizations can apply tailored protection measures. Additionally, training employees on data handling best practices and the importance of cybersecurity can significantly reduce the risk of data loss. Regular audits and assessments are also essential for ensuring that DLP measures are effective and aligned with evolving threats.
Data Leak Prevention Software
Data leak prevention (DLP) software is designed to protect sensitive information from being exposed or misused. This type of software plays a crucial role in preventing data breaches and ensuring compliance with regulations such as GDPR and HIPAA. DLP solutions work by monitoring data flows, enforcing policies, and blocking unauthorized data transmissions.
When selecting DLP software, organizations should consider features such as content inspection, endpoint protection, and reporting capabilities. Effective DLP solutions can identify sensitive data across various platforms, including cloud services and on-premise systems. By implementing a comprehensive DLP strategy, organizations can significantly reduce the risk of data leaks and enhance their overall security posture.
Best Network Security Software 2024
As cyber threats evolve, the need for robust network security software becomes increasingly critical. The best network security software of 2024 will likely include advanced features such as AI-driven threat detection, machine learning capabilities, and integrated response mechanisms. Organizations should look for solutions that provide comprehensive protection against both known and emerging threats.
Key considerations when evaluating network security software include ease of deployment, scalability, and integration with existing security tools. Solutions that offer centralized management and reporting can simplify security operations and enhance visibility across the network. Additionally, regular updates and support from the vendor are essential for maintaining an effective security posture in an ever-changing threat landscape.
Best Network Vulnerability Scanner
Network vulnerability scanners are essential tools for identifying and addressing security weaknesses within an organization's infrastructure. The best network vulnerability scanners offer comprehensive scanning capabilities, providing organizations with insights into potential vulnerabilities before they can be exploited by malicious actors.
When selecting a vulnerability scanner, organizations should consider factors such as ease of use, reporting capabilities, and integration with other security tools. Effective scanners should provide detailed reports that prioritize vulnerabilities based on risk and offer remediation guidance. Regular scanning and assessment are crucial for maintaining a strong security posture and ensuring compliance with industry regulations.
Best Antivirus for Business Networks
Choosing the best antivirus solution for business networks is vital for protecting against malware and other cyber threats. The ideal antivirus software should offer comprehensive protection, including real-time scanning, automated updates, and advanced threat detection capabilities. Additionally, it should be easy to deploy and manage across multiple devices within the organization.
When evaluating antivirus solutions, organizations should consider features such as web filtering, email security, and firewall integration. Solutions that offer centralized management can streamline security operations and provide visibility into the overall security posture of the organization. Regular updates and support from the vendor are essential to ensure that the antivirus software remains effective against new and evolving threats.
Explore

Navigating the Maze: Essential Insights into Graduate Student Loans for a Brighter Future
Best Network Security Providers for Small Businesses

Best Personal Injury Lawyers Near You: Expert Legal Insights

Empowering Enterprises: The Essential Guide to Application Software for Business Success

Shielding Your Business: The Essential Guide to Contractor's Insurance

Navigating the Waters: Your Essential Guide to Flood Insurance Quotes

Essential Guide to Choosing the Right Online Marketing Agency

Unlocking Online Success: The Ultimate Guide to Must-Have SEO Software Tools
